HashiCorp Boundary Enterprise Crack
HashiCorp Boundary Enterprise 0.15.4 Crack is a cutting-edge solution designed to redefine the way organizations manage access to their critical infrastructure. As a comprehensive access management platform, HashiCorp Boundary Enterprise Full Crack introduces a zero-trust security model, ensuring secure access to internal systems without the need for a traditional VPN. Whether you’re a DevOps professional, IT administrator, or security expert, HashiCorp Boundary Enterprise Free Crack offers a streamlined and efficient approach to access management, providing granular control over user permissions and enhancing overall network security. Say goodbye to complex network setups and embrace the simplicity and security of HashiCorp Boundary Enterprise for your access management needs.
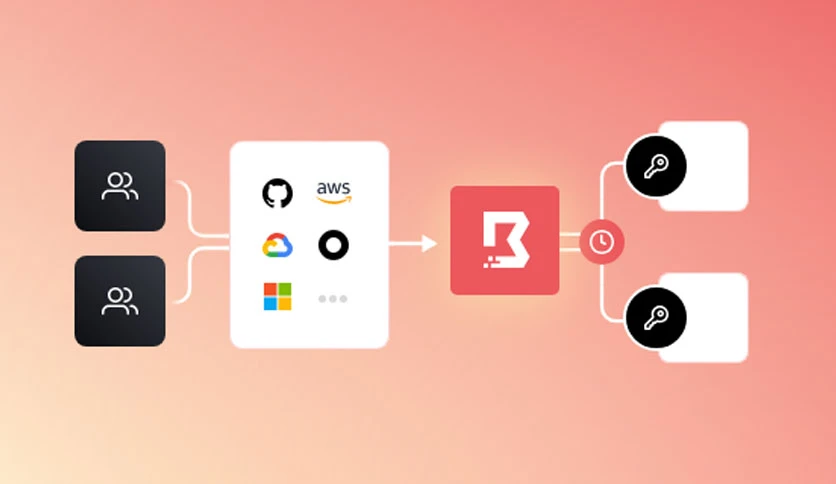
Explore the extensive features that set HashiCorp Boundary Enterprise Mac Crack apart as a leader in the realm of access management. The platform introduces dynamic identity-based access, allowing organizations to define access policies based on user identities rather than traditional network constructs. With fine-grained access control, administrators can define precise access rules, ensuring that users only access the resources they need for their specific roles. HashiCorp Boundary Enterprise supports multi-cloud environments, providing flexibility in managing access across diverse infrastructure. Its robust auditing and logging capabilities empower organizations to maintain visibility into access patterns, facilitating compliance and enhancing security postures. Experience the future of access management with HashiCorp Boundary Enterprise Cracked, where simplicity meets security in the world of network access.
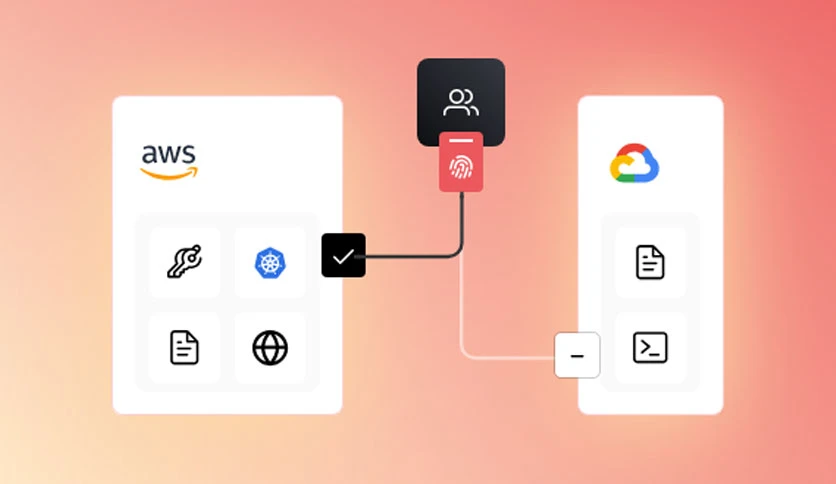
HashiCorp Boundary Enterprise Crack Features:
1. Zero-Trust Security Model
Embrace a zero-trust security model, allowing secure access to internal systems without relying on traditional VPNs, enhancing overall network security.
2. Dynamic Identity-Based Access
Introduce dynamic identity-based access, enabling organizations to define access policies based on user identities for a more flexible and scalable access management approach.
3. Fine-Grained Access Control
Implement fine-grained access control, giving administrators the ability to define precise access rules to ensure users access only the resources necessary for their specific roles.
4. Multi-Cloud Support
Support multi-cloud environments, providing flexibility in managing access across diverse infrastructure and simplifying access management in complex, distributed systems.
5. Auditing and Logging
Enhance visibility into access patterns with robust auditing and logging capabilities, empowering organizations to maintain compliance and strengthen security postures.
System Requirements
Operating System: Compatible with Windows 7, 8, and 10.
Processor: A 1 GHz or higher Intel
RAM: 1 GB of RAM
Hard Disk Space: 100 MB of free space
HashiCorp Boundary Enterprise 0.15.4 100% Working Keys 2024
HashiCorp Boundary Enterprise Serial Key
SV97U-ER0L4-5IVF3-5YZCA-7F2SR
082QP-DDJ8S-P8MA9-5NWP3-3Z06A
HashiCorp Boundary Enterprise License Key
K6RA2-23PW9-S61KA-JQ01O-6Q9J4
N89VP-TGA3N-GRQ0Q-KVS39-PDPR7
HashiCorp Boundary Enterprise Product Key
7MC8H-I7J00-E9P03-H80D0-79UNX
L36A3-B3I2W-XSP7R-4APBK-040AY
HashiCorp Boundary Enterprise Activation Code
PA8C7-2ZFLK-CN0K3-GR3U4-BMRV3
5MEVO-MGQ3F-ODDRW-L89O6-DHA21
How To Crack & Install HashiCorp Boundary Enterprise 0.15.4
- First download the latest version.
- Uninstall the previous version with Smarty Uninstaller Crack, If Installed.
- Note Turn off the Virus Guard.
- After downloading Unpack or extract the rar file and open setup (use Winrar to extract).
- Install the setup after installation close it from everywhere.
- Please use Keygen to activate the program.
- After all of these enjoy the HashiCorp Boundary Enterprise 0.15.4 Crack Latest Version 2024.
